HELLO friends
When i first read about hashing and encryption i got little bit confused and was thinking "WHAT IS THE DIFFERENCE BETWEEN THEM". Actually I got introduce with these two terms when i was configuring my routers password specially when i was configuring ppp authentication.After that i decide to explore about these two stuffs
let start with brief analysis of both terms and how they are different with each other.
Hashing an encryption both of them are use to hide the original contents of data into some unrecognizable format. so it is clear that both of them are use to protect the data from intruders.
The basic difference is that ENCRYPTION is a reversible process while HASHING is a irreversible process.
Now i will discuss in details regarding algorithm of each one.
CASE 1 -HASHING
Basically, this hash algorithm is a formula used to convert a variable-length message into a fixed-length hash. It is also important to understand that this is a one-way function. A message can produce a hash, but a hash cannot produce the original message. After the hash is calculated, it is sent over the network together with the message. At the other end, the receiver performs the same action. It sends the message and the shared key through the hash algorithm and then compares the two hashes to verify whether they match.


Now i will tell you what is going on .As you can see that we have a plain text "JOHN" and we have to convert it into cipher text with hashing algorithm. suppose Y is our hashing table algorithm.It always convert plain text "john" into "XYZ" cipher text.Everytime cypher text will be "XYZ".
NOTE-Please pay attention here in third figure that cypher text "XYZ" is not going to convert into "JOHN"
plain text.so it is not easy or intruder to catch private data.
In the above figure(where routers are shown) it is application of hashing algorithm.
CASE 2 -ENCRYPTION.
Now it is time for encryption fundamentals.In encryption also plain text is converted into cypher text and it is reversible process.i will explain with the help of figure below
.


refer to above (left) figure ."JOHN" is our plain text and "X" is our encryption algorithm and what we found here every time algorithm"X" will produce different cypher text. As we can see from figure first time cipher text was"XYZ" and second time it is "ABC".so we can conclude that every time it will produce different cipher text unlike HASHING ALGORITHM.
refer to above (right) our cipher text "XYZ" is going to convert into plain text "JOHN" by using encryption algorithm "X".
ENCRYPTION has two class-
1> SYMMETRIC ENCRYPTION-less secure,both peer uses same key yo encrypt and decrypt the data .
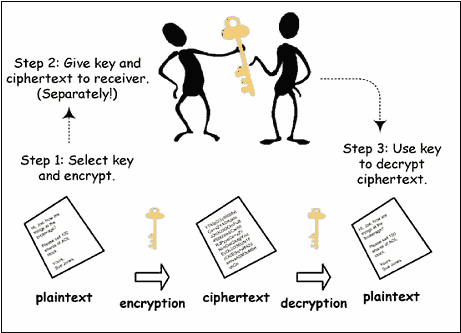
2> ASYMMETRIC ENCRYPTION -more secure ,each peer uses different key to encrypt or decrypt the
data
HOPE THIS DOCUMENT WILL PROVE
USEFUL TO ALL TECH GEEKS.
now i am not anymore confused because i got the concept.
BYE FOR NOW.

No comments:
Post a Comment